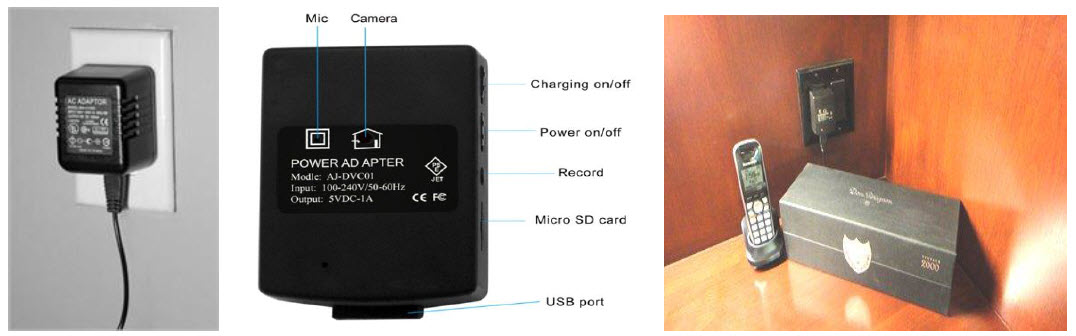
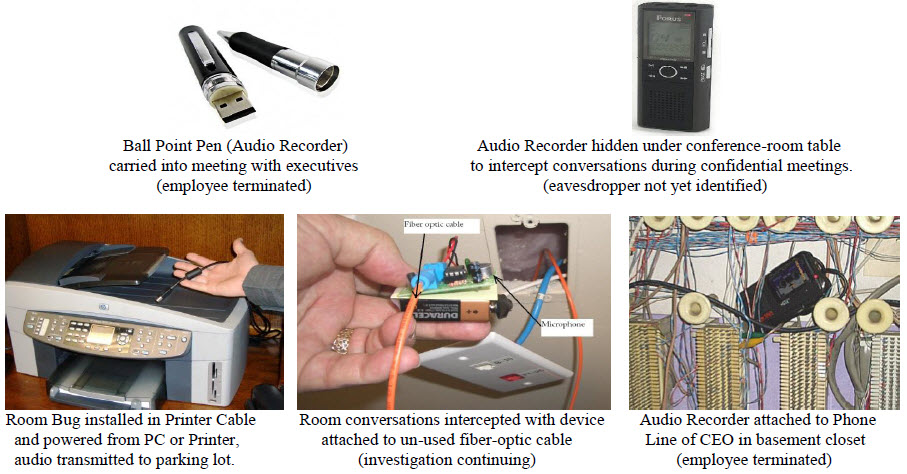
13 Sneaky Ways FBI Agents Protect Their Homes
Who better to get advice on home protection than FBI agents who have studied and observed the minds of criminals? Even better? These home security tips are totally doable!
“Oftentimes, crime can be discouraged by the mere presence of an alert neighbor,” says Douglas Kane, president of Risk Control Strategies and a 27-year veteran of the […]